Difference between revisions of "Revue software root"
| (14 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
== WARNING == | == WARNING == | ||
The links on this page contain the until now unreleased Revue root. This is being released as a way to allow the more skilled members of the community to look at. The root is incredibly unstable and we are providing it unpackaged to prevent it from being used by someone who may end up damaging their box. As bliss described it, “it is like punching the device in the face while telling it that it’s not getting hit”. If you are looking to get root to help achieve some form of optimal Android experience from the box, then please wait for a better packaged version with persistence. If you are technically savy and are willing to risk damaging your box, gambling on how skilled you are, then feel free to give it a shot. Please note that you are likely to brick your device much like we have bricked ours many times (but we have fancy-pants hardware recovery mechanisms). | The links on this page contain the until now unreleased Revue root. This is being released as a way to allow the more skilled members of the community to look at. The root is incredibly unstable and we are providing it unpackaged to prevent it from being used by someone who may end up damaging their box. As bliss described it, “it is like punching the device in the face while telling it that it’s not getting hit”. If you are looking to get root to help achieve some form of optimal Android experience from the box, then please wait for a better packaged version with persistence. If you are technically savy and are willing to risk damaging your box, gambling on how skilled you are, then feel free to give it a shot. Please note that you are likely to brick your device much like we have bricked ours many times (but we have fancy-pants hardware recovery mechanisms). | ||
==About== | ==About== | ||
[[File:Nandpwn.png|350px|left|border]]<br style="clear: both" /> | |||
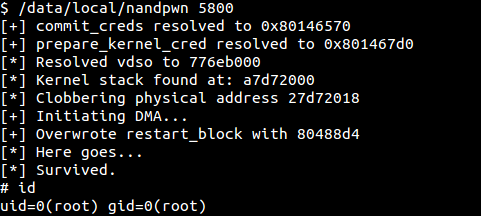
The Nandpwn package was created by Dan Rosenberg (@djrbliss) with remote testing on Exploitee.rs team member boxes (Dan doesn't actually own a revue). The exploit is highly complex and leverages a world readable device driver left open by Logitech. | |||
===About nandpwn=== | ===About nandpwn=== | ||
A local privilege escalation exploit for the Logitech Revue that leverages the ability to map the hardware registers of the NAND flash controller in conjunction with a Linux kernel information leak to clobber kernel memory in a way that allows gaining privileges. | |||
This exploit is highly unstable. Although it has never caused any permanent damage in testing, I take no responsibility if this turns your device into a brick. In addition, it is known to only succeed a fraction of the time, so you will probably have to try it repeatedly, and some of those attempts may cause your device to freeze (which can be solved by a reboot). | |||
===Exploit Flow=== | ===Exploit Flow=== | ||
| Line 20: | Line 20: | ||
===About codesign=== | ===About codesign=== | ||
Once you have root, this can be run to disable code signing enforcement so custom kernel modules can be run. No known issues were observed during testing. | |||
===About blockwrite=== | ===About blockwrite=== | ||
'''NOVICES DO NOT USE!''' Remaps a specified block device as writable at both the MTD and block layers, to allow flashing a replacement. No known issues were observed during testing. | |||
==Work In Progress== | ==Work In Progress== | ||
===Hurdles=== | ===Hurdles=== | ||
*ADBD designed to never run as root. | *ADBD designed to never run as root. (Completed) | ||
*Signed /system, /boot, kernel, recovery, bootloader | *Signed /system, /boot, kernel, recovery, bootloader | ||
*nosuid /cache, /data, /sdcard | *nosuid /cache, /data, /sdcard | ||
| Line 33: | Line 33: | ||
===Bugs=== | ===Bugs=== | ||
This is unstable and should be seen as more of a POC (Proof of concept) than a public release. This exploit | *'''Persistence''' - This is unstable and should be seen as more of a POC (Proof of concept) than a public release. This exploit is not persistent between boots (which means you will have to run this each time you start the device). We are working on fixing this but are having to jump through quite a few hurdles because of the signed partitions. We will update this page with progress when/if we come up with a work around. | ||
===Support=== | |||
Due to the complexity of the bug and the agreement that this shouldn't currently be used by the public for general purpose use, neither us nor Dan Rosenberg will be offering support for this package until we have a public release which offers persistence. Even when we do have a package released, Dan will still be too busy to field questions and any help will need to come from our forums or the #Exploiteers channel on freenode. But just an early warning, if you brick your box you will either need to purchase and attach a NAND programmer, donate the box to one of us, or accept the fact that you now have an expensive paperweight. | |||
==Exploiting== | ==Exploiting== | ||
| Line 42: | Line 45: | ||
===Building the code=== | ===Building the code=== | ||
We are not posting how to build the code as if you are unable to build an x86 binary you probably shouldn't be attempting this root in the first place. | We are not posting how to build the code as if you are unable to build an x86 binary you probably shouldn't be attempting this root in the first place. | ||
===Video=== | |||
[http://www.youtube.com/watch?v=mo3IlbpfoFk Video of NandPwn in action] | |||
===Download=== | ===Download=== | ||
[https://github.com/djrbliss/revue/tree/master/nandpwn NandPwn] | [https://github.com/djrbliss/revue/tree/master/nandpwn NandPwn] <-- Root Exploit | ||
[https://github.com/djrbliss/revue/tree/master/codesign Codesign] <-- Enables code Signing | |||
[https://github.com/djrbliss/revue/tree/master/blockwrite BlockWrite] <-- Allows writing to RO partitions (Beware most partitions are signed, modifications will cause a brick) | |||
[[Category:Logitech]] | |||
Latest revision as of 20:23, 3 January 2017
WARNING
The links on this page contain the until now unreleased Revue root. This is being released as a way to allow the more skilled members of the community to look at. The root is incredibly unstable and we are providing it unpackaged to prevent it from being used by someone who may end up damaging their box. As bliss described it, “it is like punching the device in the face while telling it that it’s not getting hit”. If you are looking to get root to help achieve some form of optimal Android experience from the box, then please wait for a better packaged version with persistence. If you are technically savy and are willing to risk damaging your box, gambling on how skilled you are, then feel free to give it a shot. Please note that you are likely to brick your device much like we have bricked ours many times (but we have fancy-pants hardware recovery mechanisms).
About
The Nandpwn package was created by Dan Rosenberg (@djrbliss) with remote testing on Exploitee.rs team member boxes (Dan doesn't actually own a revue). The exploit is highly complex and leverages a world readable device driver left open by Logitech.
About nandpwn
A local privilege escalation exploit for the Logitech Revue that leverages the ability to map the hardware registers of the NAND flash controller in conjunction with a Linux kernel information leak to clobber kernel memory in a way that allows gaining privileges.
This exploit is highly unstable. Although it has never caused any permanent damage in testing, I take no responsibility if this turns your device into a brick. In addition, it is known to only succeed a fraction of the time, so you will probably have to try it repeatedly, and some of those attempts may cause your device to freeze (which can be solved by a reboot).
Exploit Flow
- Use /dev/devmem to map NAND controller's hardware registers into address space
- Leverage kernel info leak to resolve virtual address of current process' kernel stack
- Write to hardware registers to trigger DMA on top of offset from base of kernel stack
- Since addr_limit is raised (hopefully), can read()/write() to write/read arbitrary kernel memory
- Fixup sysenter_return, overwrite restart_block function pointer to point to payload
- Trigger function pointer to escalate privileges and win!
About codesign
Once you have root, this can be run to disable code signing enforcement so custom kernel modules can be run. No known issues were observed during testing.
About blockwrite
NOVICES DO NOT USE! Remaps a specified block device as writable at both the MTD and block layers, to allow flashing a replacement. No known issues were observed during testing.
Work In Progress
Hurdles
- ADBD designed to never run as root. (Completed)
- Signed /system, /boot, kernel, recovery, bootloader
- nosuid /cache, /data, /sdcard
- nodev /cache, /data, /sdcard
Bugs
- Persistence - This is unstable and should be seen as more of a POC (Proof of concept) than a public release. This exploit is not persistent between boots (which means you will have to run this each time you start the device). We are working on fixing this but are having to jump through quite a few hurdles because of the signed partitions. We will update this page with progress when/if we come up with a work around.
Support
Due to the complexity of the bug and the agreement that this shouldn't currently be used by the public for general purpose use, neither us nor Dan Rosenberg will be offering support for this package until we have a public release which offers persistence. Even when we do have a package released, Dan will still be too busy to field questions and any help will need to come from our forums or the #Exploiteers channel on freenode. But just an early warning, if you brick your box you will either need to purchase and attach a NAND programmer, donate the box to one of us, or accept the fact that you now have an expensive paperweight.
Exploiting
Required Tools
- ADB (Android Debug Bridge)
- x86 Compiler
Building the code
We are not posting how to build the code as if you are unable to build an x86 binary you probably shouldn't be attempting this root in the first place.
Video
Download
NandPwn <-- Root Exploit
Codesign <-- Enables code Signing
BlockWrite <-- Allows writing to RO partitions (Beware most partitions are signed, modifications will cause a brick)