Netgear Push2TV (PTV3000)
From Exploitee.rs
Jump to navigationJump to search
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."
This page will be dedicated to a general overview, descriptions, and information related to the Netgear Push2TV.
Purchase
Buying devices is expensive and, in a lot of cases our testing leads to bricked equipment. If you would like to help support our group, site, and research please use one of the links below to purchase your next device. Purchase the Netgear Push2TV at Amazon
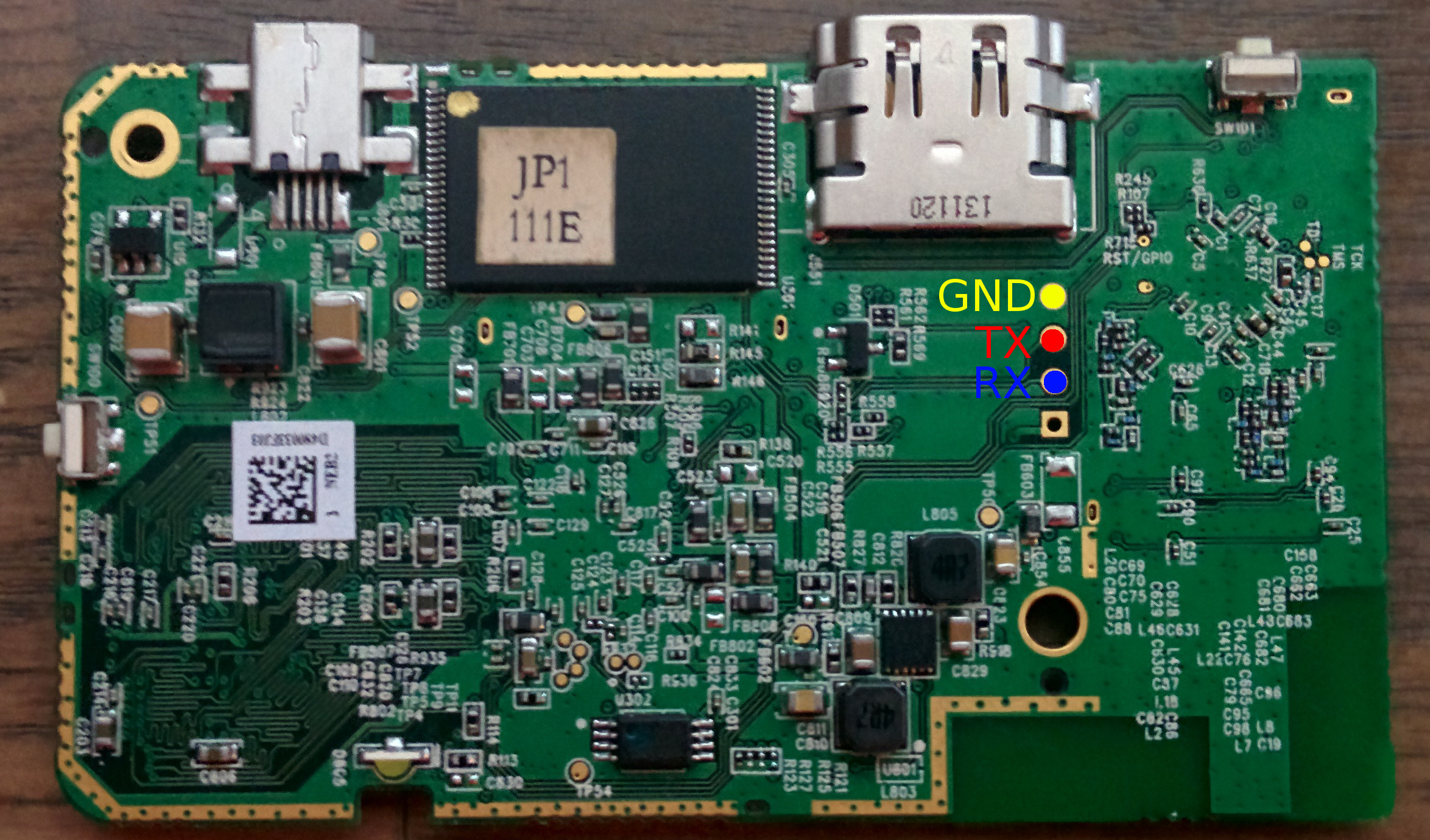
Pinout
Exploitation
There are multiple vulnerabilities in the Netgear Push2TV (PTV3000)
- Connecting to the UART per the input above, press the spacebar while booting to interrupt the bootloader, U-Boot. From here you can execute your own bootloader commands. "setenv bootargs init=/bin/sh" will drop you to a root shell
- If you miss that, via UART again, a root console is active for 2-3 seconds after booting. As long as you enter your commands while it boots, they will be executed.
- There is also a command injection in the web interface. By inserting a command in the box nickname field (say ;reboot;) the command will be executed as root.
- Finally, the SPI flash chip holds the U-Boot environment, it can be reflashed to load a modified environment