Vizio Smart TV (VF553XVT)
"Although the information we release has been verified and shown to work to the best our knowledge, we cant be held accountable for bricked devices or roots gone wrong."
This page will be dedicated to a general overview, descriptions, and information related to the Vizio Smart TV (VF553XVT).
Images
Exploitation
A Local Command Execution vulnerability exists in a series of Vizio Smart TV's, among others, that allows arbitrary commands to be run as root.
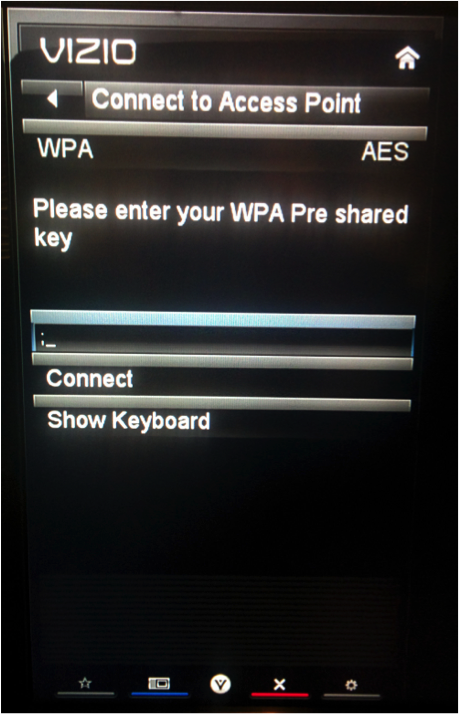
The LCE is found in the Wifi password field. Since the field is only accessible when the TV is offline, we will need to utilize a USB-UART device. Using that, we can create a shell with root access, settings 9600,8n1.
First enter the command below, it creates a character device pointing to the USB UART that we can talk to:
;mknod /tmp/gtvhacker c 188 0;
Next enter the command below, it pipes out input and output from the UART, to the character device, to the root shell:
;bash 2>/tmp/gtvhacker>/tmp/gtvhacker</tmp/gtvhacker;bash;